BitKit v1.0.3 – Crack , Hack & Hunting PrivateKey Bitcoin

Hunting and Brute Forcing With 3 Method For Private Key , Mnemonic and DEC Bitcoin Wallet.
- BitKit Order Now
-
Introduction
-
Performance
-
Technologies used
-
Methods Random Private Keys , Mnemonic’s, Integer (Number).
-
Teaching parts
-
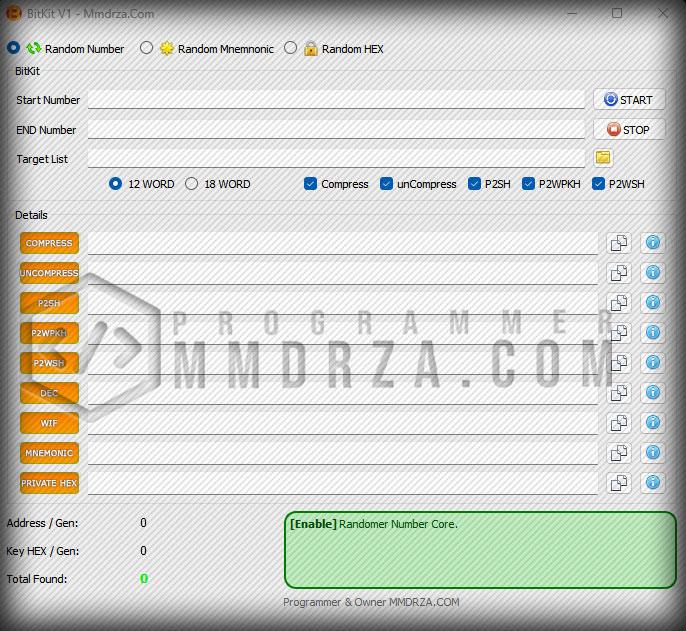
— Random Integer
-
— Random Mnemonic
-
— Random Hex (SHA256)
-
— Start Number
-
— End Number
-
— Target List
-
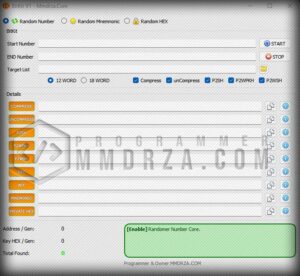
— 12 Word
-
— 18 Word
-
— Compress Address Bitcoin
-
— Un Compress Address Bitcoin
-
— Address BTC P2SH
-
— Address BTC P2WSH
-
— Address BTC P2WPKH
-
— WIF
-
— Mnemonic
-
— Private Key (hex)
-
— Start and Stop
-
— Copy Button
-
— About Button
-
Screen Record (video)
-
Tutorial Video
-
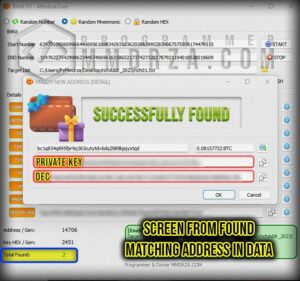
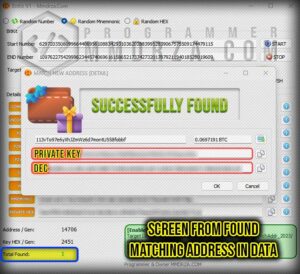
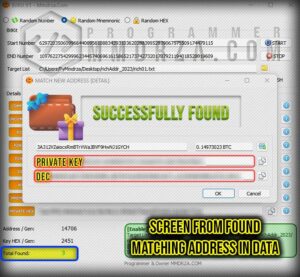
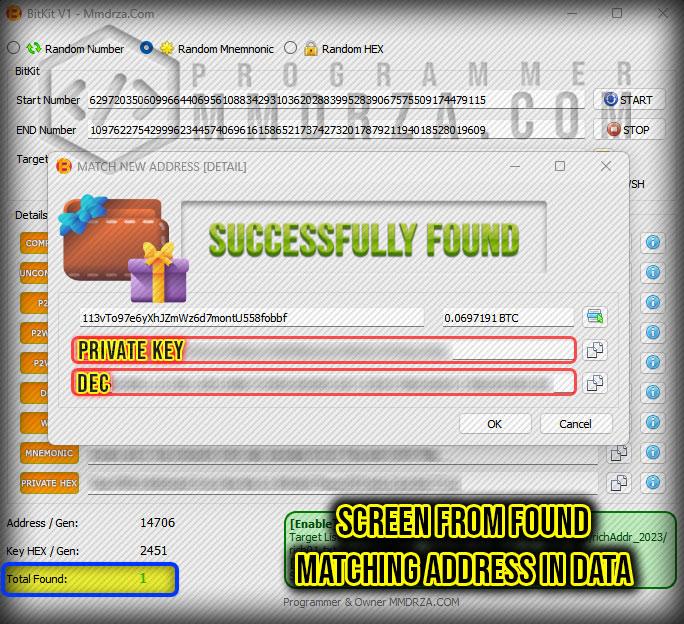
Found & Match 8 Wallet Detail’s (video)
A private key is a series of letters and numbers that gives you access to the bitcoin kept in a particular wallet. Because anyone with access to your private key could possibly access and use your money, it is crucial to keep it secure and discreet. for more detail a private key can follow this article : private key wallet the ultimate guide
Introduction
Many software’s and scripts have been published in the field of recovering or cracking the private key of the Bitcoin wallet, most of which are intended to deceive and defraud new and uninformed people. As you know, creating a private key in the past (that is, until today) was incredible, being able to recover the private key in a very short period of time, and the minimum time with the best systems has been over 50 years, if our private key is SH 256 coded. Was .
Bitkit V1 For Hunting And Crack Private Key Wallet Bitcoin , Quantum Method
But now, although many people do not want me to make this software public, and they consider it worthless and think that such a method is still impossible, the release of this software with the official name of BitKit will be silenced forever. These people never decisively question their values and character and keep people in ignorance. Because this will cause a big blow that will be remembered by me today in the history of cryptocurrencies with a nightmare. Because it is true that the value of the software is very high, but I will make this software available to the public at a reasonable and unbelievable price for the access of all sections of the society and the middle class who cannot pay for the software. You may not believe that I will not and will not fully publish my method that succeeded in breaking private keys at a high speed, but I will give a short explanation about it to question all the interpretations of Bitcoin and cryptocurrency theorists.
When a private key is created by different methods, you think for the person who created it or to say more clearly. Is it difficult for the programmer who generated the private key generation script to reverse the generation method? 😀
If you are a programmer and you are reading this article, I gave you a big clue and a big help that I worked for years and stayed awake many nights to find the answer, and now you can go to the end with this clue of mine and find out. What method did I use to crack a large number of addresses with Bitkit?
Performance
Reverse encryption and non-repeatable private key:
generation of Bitcoin Volt private key from numbers and letters in a random and non-repeating way in a private conversion string and creating WIF and finally that private key (SHA-256).
Generation of unordered, repeated and unordered numbers starting and ending at the beginning of the program.
Creating and creating a compressed address and that compressed Bitcoin and P2SH type address and P2wsh , P2wpkh …
Creating and obtaining WIF and SHA-256 private keys and finally 12 and 18 words of the primary private key string that is highly secure for each user.
Creating randomly and randomly with a very high speed in checking the data, and converting the private key into an address and checking addresses of different types with the total of the addresses uploaded by the user. will be).
A collection of bitcoin wallet addresses with high inventory and value in the form of a text file and automatic file update weekly.
Prediction of daily breaking of 3 private keys in the worst and weakest systems with weak processes. I announced the minimum number.
Technologies used
The latest methods and the most professional techniques in the world using quantum process technology in fast recovery and high-speed calculation are the distinctive features of BitKit, which has made the components of this powerful software attractive to everyone.
Methods Random Private Keys , Mnemonic’s, Integer (Number).
The methods that you can perform your operations with Bitkit include random numbers: in this method, the keys are randomly calculated as random numbers, which has greatly increased the percentage of finding similar addresses from the data with the techniques used.
Teaching parts
Before I introduce all the parts of the software, I remind you that, unfortunately, other colleagues may claim to have similar software to you, but since the number of these people is very small and most of them get their ideas from They copy the software here and ask me for the latest methods to make them public. So let me assure you right now, if you still doubt our ability, it is better to watch the video at the end of this post to see what the result of my software working with others is.
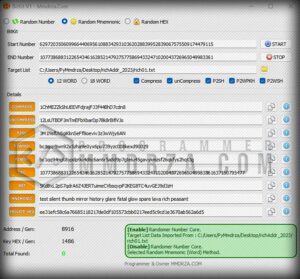
Random Number :
If you want to choose the fastest method and get rich faster, choose random numbers, in this section all data and calculations are done randomly And randomly, these numbers are converted into the private key, which has the highest percentage of finding among the options, but the only difference with the other two items is that it does not show you the mnemonic.
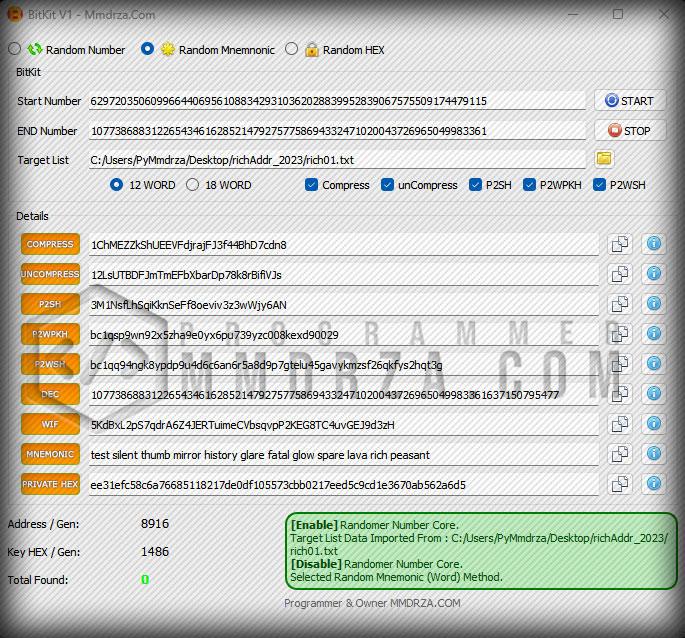
Random Mnemonic :
The second part is generating the software for the private key from random mnemonics, the standard number of which is 12 and 18 words, which you can choose yourself in the relevant section, but it is set to 12Word by default.
Random Hex :
It is the same private production in the form of hex and random, which has a good speed and does not repeat. Note that this software does not provide you with a duplicate private key from any of the methods mentioned above and does not bother itself to create it; Add this difference to the hundreds of differences between this software and similar ones.
In similar software, it is better if you want to check them yourself and see if they will give you a private key in one day if you leave them on for 24 hours?? They won’t give, because they can’t and their programmer just copies and has no experience.
Start Number And End Number :
The first field part, which is the start number, is related to the numbers from which the creation of the private key started, and in the end number part, you will also see the numbers that are the last numbers of our range, and between the start and the end of them, a number is created randomly. which is a clear method used in many online and software wallet services.
Target List File :
An important part of the software is the target list section, which requires a text file containing bitcoin addresses with a high balance, one address is inserted in each line, and by pressing the folder button next to it, you can select the desired file in the opened window. do
12 , 18 word :In the section of mnemonics that you choose, it is obligatory to choose the number of relevant words, which is 12 by default, but you can also choose 18. This depends on your taste and I suggest you leave it on the default option and don’t change it.
Bitkit V1 For Hunting And Crack Private Key Wallet Bitcoin , Quantum Method
Compress & UnCompress Address Wallet Bitcoin :
In this section, you can see the compressed address of Bitcoin. We would like to explain it to you. We say:
A Bitcoin address can be compressed to save space when sending or storing it. Compressed addresses use a different format for the public key that allows them to be shorter, usually around 33 characters. To compress a Bitcoin address, you can use a program or website that supports the compression of addresses. Some wallets also have this feature built-in. To compress an address, you will need the public key associated with it. The public key is a long string of letters and numbers that is derived from the private key, which is used to sign transactions and prove ownership of the funds. To compress the address, the public key is run through a specific algorithm, which produces a shorter version of the key that can be used to generate the address. It is important to note that compressed and uncompressed addresses are interchangeable and represent the same funds. You can use either format when sending or receiving payments, and the funds will still be credited to the same address. The choice of which format to use is up to the user and is mainly a matter of preference or convenience.
Uncompress Address :
An uncompressed Bitcoin address is a version of a Bitcoin address that uses an uncompressed public key. An uncompressed address is longer than a compressed address, usually around 65 characters, because it includes the full, uncompressed public key.
P2SH:
The next part that the software shows you and is visible is the P2SH type address, which we would like to explain more fully:
P2SH (Pay-to-Script-Hash) is a type of Bitcoin address that is used to send funds to a script hash (address) instead of a public key hash. It allows users to send funds to a script without knowing the details of the script, making it more flexible and secure. P2SH addresses are identified by their prefix, which is “3” for mainnet and “2” for testnet. They are typically longer than regular Bitcoin addresses, which have a prefix of “1” for Mainnet and “m” or “n” for Testnet.
P2SH addresses can be used to send funds to a Multisignature address, which requires more than one private key to sign a transaction and spend the funds. They can also be used to send funds to a script that has more complex conditions for spending, such as time locks or atomic swaps. To send funds to a P2SH address, the sender does not need to know the details of the script associated with the address. They only need to provide the script hash and the required amount of satoshis. The script itself is hashed and stored on the blockchain, and the funds can only be spent by providing a valid script that matches the hash and satisfies the conditions of the script.
P2WSH:
Next Section in software (BitKit) , and more detail’s :
P2WSH (Pay-to-Witness-Script-Hash) is a type of Bitcoin address that is used to send funds to a witness script hash (address) instead of a public key hash. It is an improvement over P2SH (Pay-to-Script-Hash) addresses, as it allows users to send funds to a script that is hashed and stored off-chain, in the witness data of a transaction, rather than on-chain. P2WSH addresses are identified by their prefix, which is “bc1” for mainnet and “tb1” for testnet. They are typically longer than regular Bitcoin addresses, which have a prefix of “1” for mainnet and “m” or “n” for testnet.
P2WSH addresses can be used to send funds to a multisignature address, which requires more than one private key to sign a transaction and spend the funds. They can also be used to send funds to a script that has more complex conditions for spending, such as time locks or atomic swaps. To send funds to a P2WSH address, the sender does not need to know the details of the script associated with the address. They only need to provide the witness script hash and the required amount of satoshis. The script itself is hashed and stored in the witness data of the transaction, and the funds can only be spent by providing a valid script that matches the hash and satisfies the conditions of the script.
P2WPKH: Next Section in software , and more detail’s :
P2WPKH (Pay-to-Witness-Public-Key-Hash) is a type of Bitcoin address that is used to send funds to a witness public key hash (address) instead of a regular public key hash. It is an improvement over P2PKH (Pay-to-Public-Key-Hash) addresses, as it allows users to send funds to a public key that is hashed and stored off-chain, in the witness data of a transaction, rather than on-chain.
P2WPKH addresses are identified by their prefix, which is “bc1” for mainnet and “tb1” for testnet. They are typically shorter than regular Bitcoin addresses, which have a prefix of “1” for mainnet and “m” or “n” for testnet.
P2WPKH addresses can be used to send funds to a single-signature address, which requires only one private key to sign a transaction and spend the funds. They are more efficient and secure than P2PKH addresses, as they take up less space on the blockchain and are less vulnerable to certain types of attacks.To send funds to a P2WPKH address, the sender only needs to provide the witness public key hash and the required amount of Satoshis. The public key itself is hashed and stored in the witness data of the transaction, and the funds can only be spent by providing a valid signature that matches the hash and proves ownership of the private key.
WIF : The next section is related to WIF, which is displayed in the software every time it is built, but if we want to explain it a little more fully and define it, we must say : A WIF (Wallet Import Format) key is a private key that is encoded in a specific format for easier import into a cryptocurrency wallet. It is a convenient way to store and manage private keys, as it can be easily imported and exported between different wallets and platforms.
A WIF key consists of the private key, encoded in base-58, and a prefix that identifies the network and the type of key. The prefix for a WIF key on the Bitcoin Mainnet is “5”, and on the Bitcoin testnet is “9” or “c”. To use a WIF key, you will need a wallet that supports this format. Most wallets allow you to import and export private keys in WIF format, either through a menu option or by entering a specific command.
To import a WIF key into a wallet, you will need to provide the key and any other necessary information, such as the password or passphrase for the wallet. The wallet will then decode the key and use it to derive the corresponding public key and address, which can be used to receive and manage the funds associated with the key. It is important to keep your WIF key secure, as it gives access to your funds and should be treated as sensitive information. You should never share your WIF key with anyone, and you should store it in a safe and secure place, such as a password manager or a physical backup.
Mnemonic : The next section is related to Mnemonic, which is displayed in the software every time it is built, but if we want to explain it a little more fully and define it, we must say : A mnemonic phrase, or mnemonic seed, is a list of words that are used as a memory aid for storing and generating the private keys of a cryptocurrency wallet. It is a convenient and secure way to back up and restore a wallet, as it can be easily written down or memorized and does not require any special equipment or software.
A mnemonic phrase consists of a series of words, typically 12, 15, 18, 21, or 24, that are generated randomly and are used to represent the private key of the wallet. Each word in the phrase corresponds to a number, and the numbers are used to generate the private key through a specific algorithm.
DEC : To put it simply, the private key is numeric and does not contain letters. which can be seen in the other part of the software and is considered one of the most important information of every wallet.
Private Key (HEX) : The next part is the private key, which I explained to you at the beginning of the post, but I will say it again to be complete: private key is a secret, alphanumeric password that is used to access and manage the funds of a cryptocurrency wallet. It is derived from a seed phrase, which is a randomly generated list of words that is used to create and restore the wallet. The private key is used to generate the public key and the address of the wallet, which are used to receive and send funds.
A private key can be encoded in different formats, such as hexadecimal (hex), base-64, or base-58. The hexadecimal format represents the private key as a string of letters and numbers, using the hexadecimal numbering system, which consists of 16 symbols: 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A, B, C, D, E, and F. The hexadecimal format is often used to represent large binary values, such as hashes or keys, in a more compact and readable form. It is also used to encode and decode data, to perform calculations, and to validate transactions. To use a private key in hex format, you will need a wallet or a program that supports this format. Most wallets allow you to import and export private keys in hex format, either through a menu option or by entering a specific command.
Bitkit V1 For Hunting And Crack Private Key Wallet Bitcoin , Quantum Method
It is important to keep your private key secure, as it gives access to your funds and should be treated as sensitive information. You should never share your private key with anyone, and you should store it in a safe and secure place, such as a password manager or a physical backup.
Great offer:
Today, with the advancement of artificial intelligence and advanced methods in the programming industry, all the impossible things of the past have become possible, and it is time to ride this wave of progress and move with it. If you are one of those people who don’t know me or haven’t used my services yet, I suggest you to use this unique software to be one of the first people who use this technique and Bitkit software and the status They change their finances.
Screen Recorder BitKit :
[+] Download High Quality Video
[+] Download Normal Quality Video
[+] Download Low Quality Video
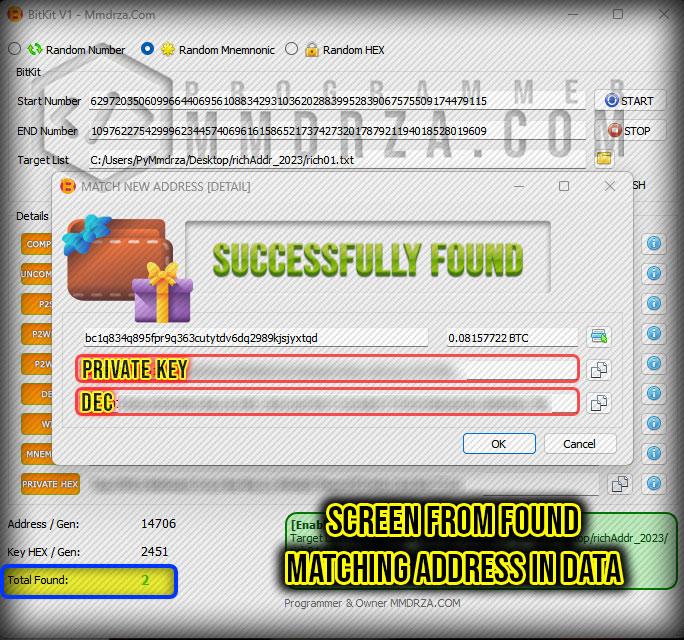
Bitkit V1 For Hunting And Crack Private Key Wallet Bitcoin , Quantum Method
BitKit – GALLERY
- bitkit v1 for hunting and crack private key wallet bitcoin , quantum method
- bitkit v1 for hunting and crack private key wallet bitcoin , quantum method
- bitkit v1 for hunting and crack private key wallet bitcoin , quantum method
- bitkit v1 for hunting and crack private key wallet bitcoin , quantum method
- bitkit v1 for hunting and crack private key wallet bitcoin , quantum method