Red Crypto Magic (Ethereum And Polkadot Private Key Crack and Hack From Mnemonic)

Red Crypto Magic (Ethereum And Polkadot Private Key Crack and Hack From Mnemonic) Python Script :
Using and applying the fastest updated and new packages (bip_utils) with the latest encoding and decoding methods .
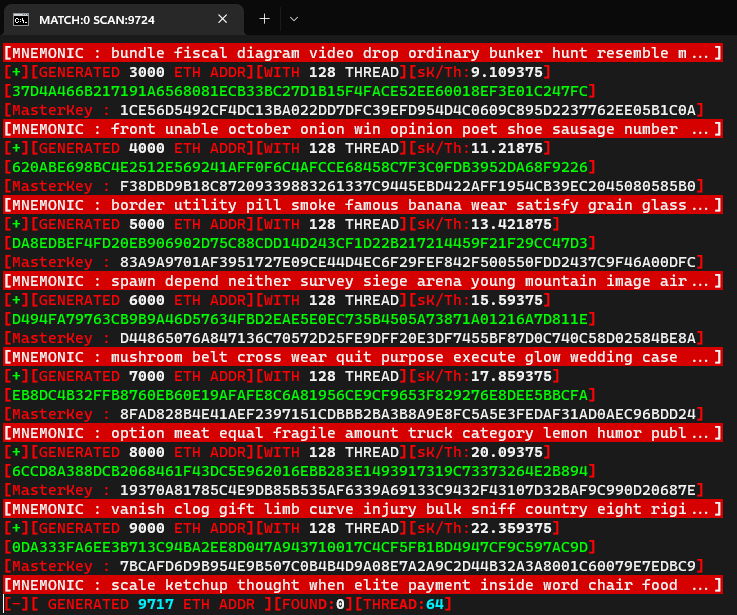
Ethereum Private Key Crack Hack Hunt Mnemonic
Polkadot (DOT) is a currency that uses the most sophisticated security methods in the creation of private keys, but now, by using a series of packages and methods, I will generate a private key and address for you in this script, after generating the private key, I will create a mnemonic. We hardcode your wallet address and then we search for that address in the list we define in it (the list of valuable wallets) at a very high speed.
Red Crypto Magic Private Key Crack And Hack From Mnemonic
The same method and tasks are also done for Ethereum, and there is no need for a special explanation.
Now you can also see other scripts about ethereum private key crack by referring to this [LINK] [Ethereum Private Key Hack and Crack Hunting With Mnemonic]
Ethereum Private Key Crack And Hack From Mnemonic SCRIPT (Source):
File : EthRedCryptoMAGIC.py
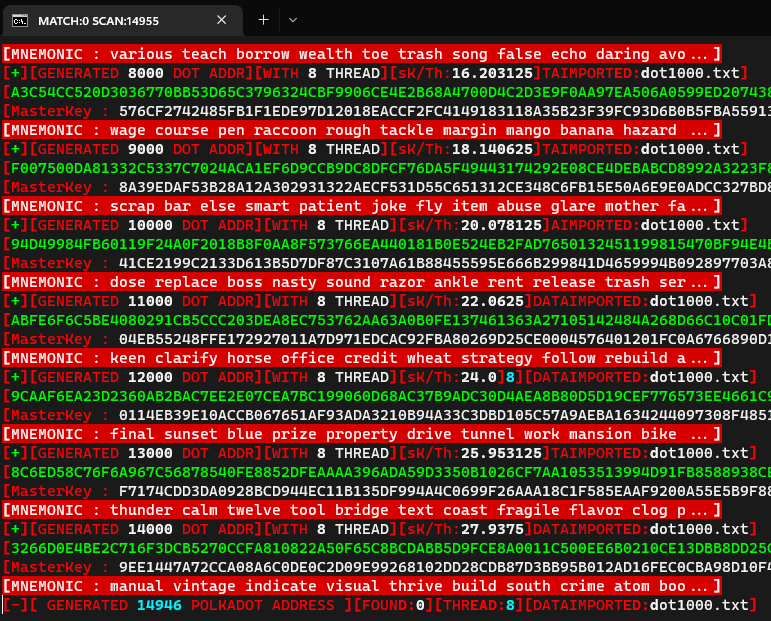
Polkadot Red Crypto Magic Private Key Crack From Mnemonic
Polkadot Private Key Crack And Hack From Mnemonic SCRIPT (Source):
File : DotRedCryptoMAGIC.py
| INSTALL PAYTHON PACKAGE’S (Windows) |
pip install bip_utils
pip install rich
pip install optparse
| INSTALL PAYTHON PACKAGE’S (Linux) |
pip3 install rich bip_utils optparse
-h OR –help Show this help message and exit
-f OR –file Ethereum Rich Address File With Type Format .TXT [Example: -f eth5.txt or –file eth5.txt]
-v OR –view Print After Generated This Number Print And Report
-n OR –thread Total Thread Number (Total Core CPU)
| Download Source File |
| EthRedCryptoMAGIC.py | |
| DotRedCryptoMAGIC.py | |
| eth5.txt | |
| dot1000.txt |
